Cloud Security Maturity Model
Cloud security maturity model. OWASP DevSecOps Maturity Model. AWS CAF groups its capabilities in six perspectives. Answers to questions about this maturity model are available in the Essential Eight Maturity Model FAQ publication.
Our framework key trends and maturity model can accelerate your journey. Get the whitepaper A Zero Trust approach for securing hybrid. The Capability Maturity Model CMM is a methodology used to develop and refine an organizations software development process.
Learn more about cloud security Learn more about threat. When a Class A appraisal is done an organization is awarded either a maturity level rating or a capability level rating. Why update the Essential Eight Maturity Model.
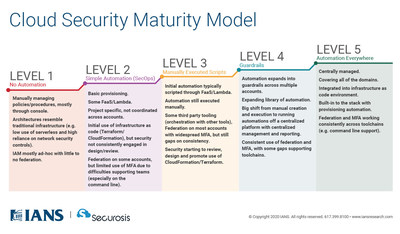
Your roadmap to cloud maturity The Cloud Maturity Assessment provides a structured approach for using the Google Cloud Adoption Framework to assess your organizations readiness for the cloud and what you can do to fill in the gaps and develop new competencies. This offline model validation step consists of the following. The model details key activities performed within Vulnerability Management on a 5-point scale.
Basic understanding of security practices Level 2. In any maturity model the path of progression is not linear and the stages can hold different meanings to each business organization. Cloud security maturity models can help accelerate the migration strategy of applications to the cloud.
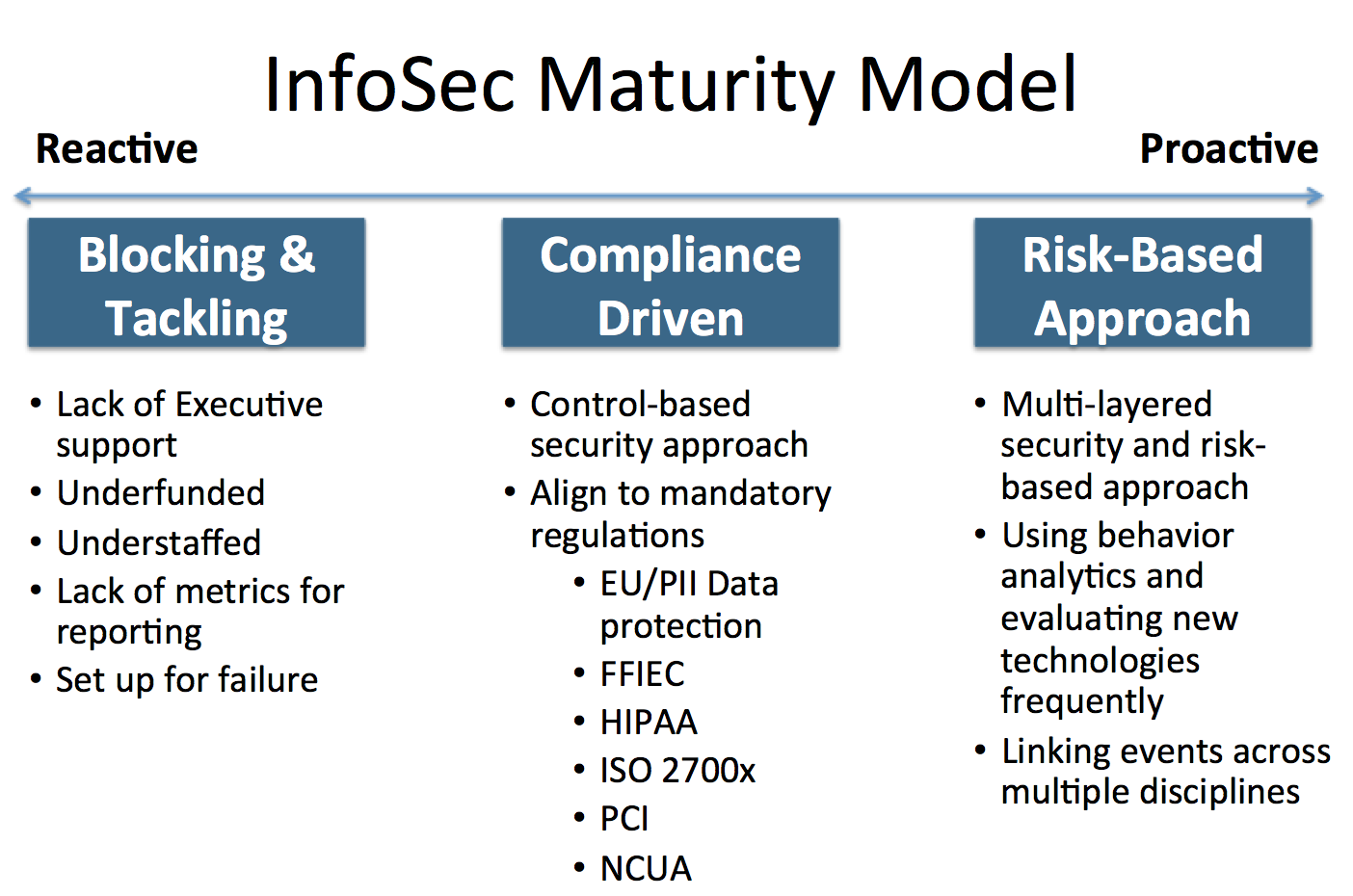
Use an integrated set of marketing cloud security and business technologies to enable end-to-end digital transformation. CMM was developed and is promoted by the Software Engineering. A Zero Trust model provides security against ransomware and cybersecurity threats by assigning the least required access needed to.
The post Useful Tips for Choosing a Cloud Security Vendor appeared first on Ermetic. From Cloud First to Cloud Smart.
This step occurs after you successfully train the model given the new data.
Advanced deployment of security practices at scale. The model details key activities performed within Vulnerability Management on a 5-point scale. A guide for what to take into account when starting to evaluate cloud security solutions. OWASP DevSecOps Maturity Model. Use an integrated set of marketing cloud security and business technologies to enable end-to-end digital transformation. AWS CAF identifies specific organizational capabilities that underpin successful cloud transformations. Dimension Sub-Dimension Level 1. Get the whitepaper A Zero Trust approach for securing hybrid. The SANS Vulnerability Management Maturity Model helps you gauge the effectiveness of your Vulnerability Management program.
Zero Trust maturity model assessment. Producing evaluation metric values using the trained model on a test dataset to assess the models predictive quality. WASHINGTON Today the Cybersecurity and Infrastructure Security Agency CISA released the Cloud Security Technical Reference Architecture TRA and Zero Trust Maturity Model for public comment. The Capability Maturity Model CMM is a methodology used to develop and refine an organizations software development process. A BSIMM assessment provides an objective data-driven evaluation that leaders seeking to improve their security postures can use to base decisions about resources time budget and priorities. CMM was developed and is promoted by the Software Engineering. Proceed to the.





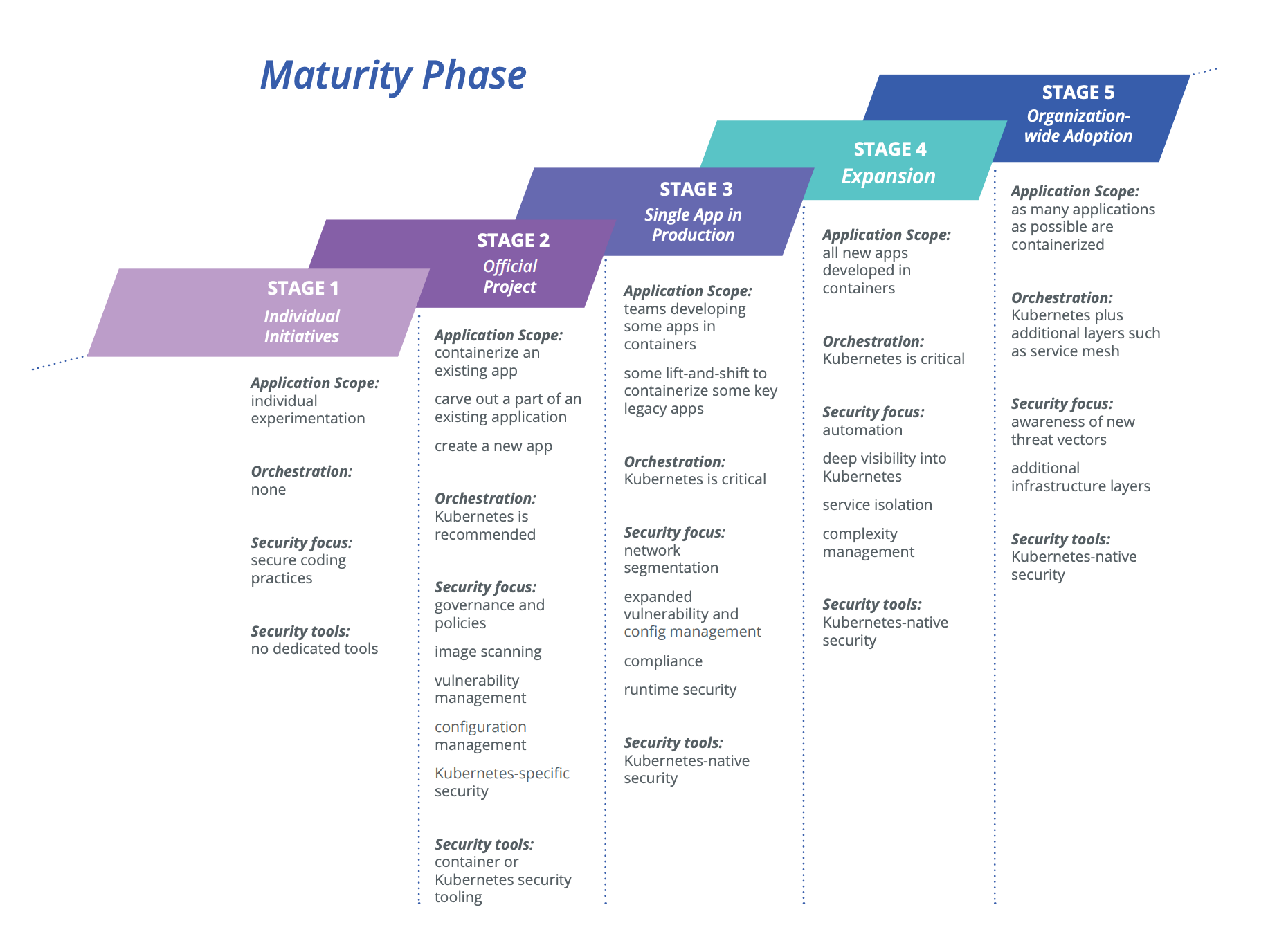




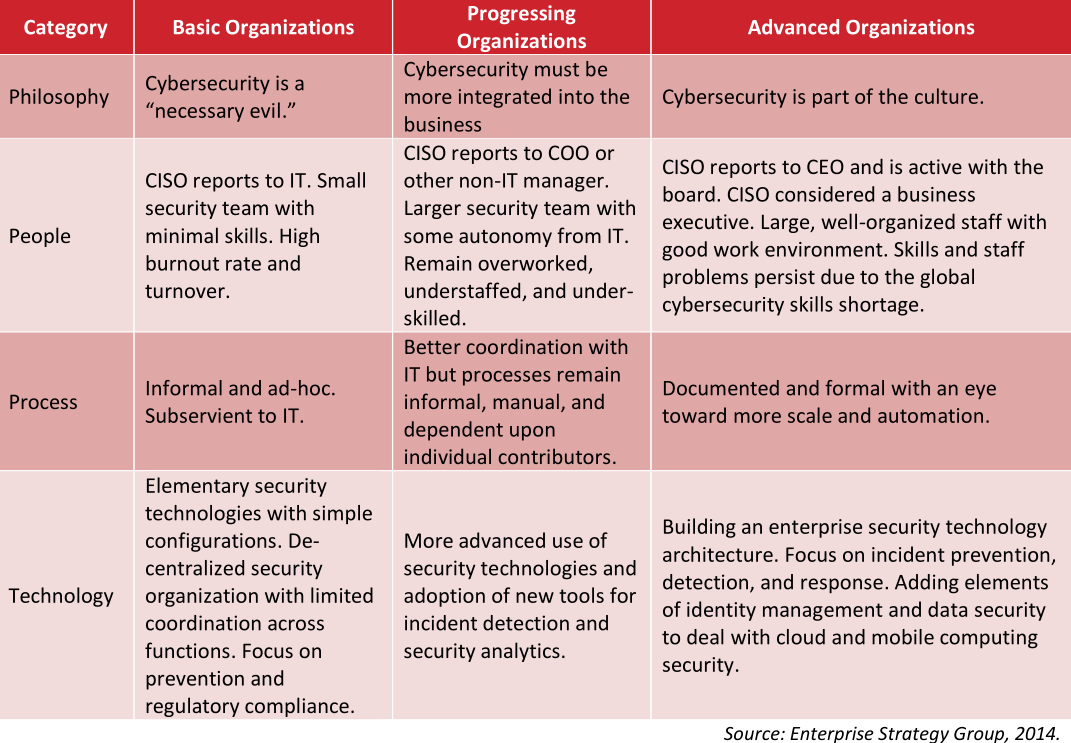


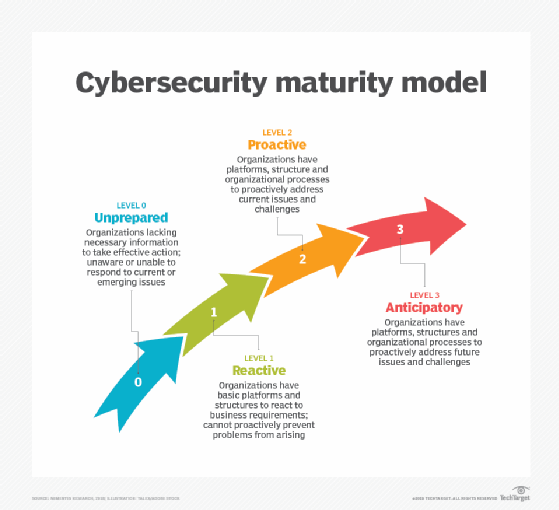



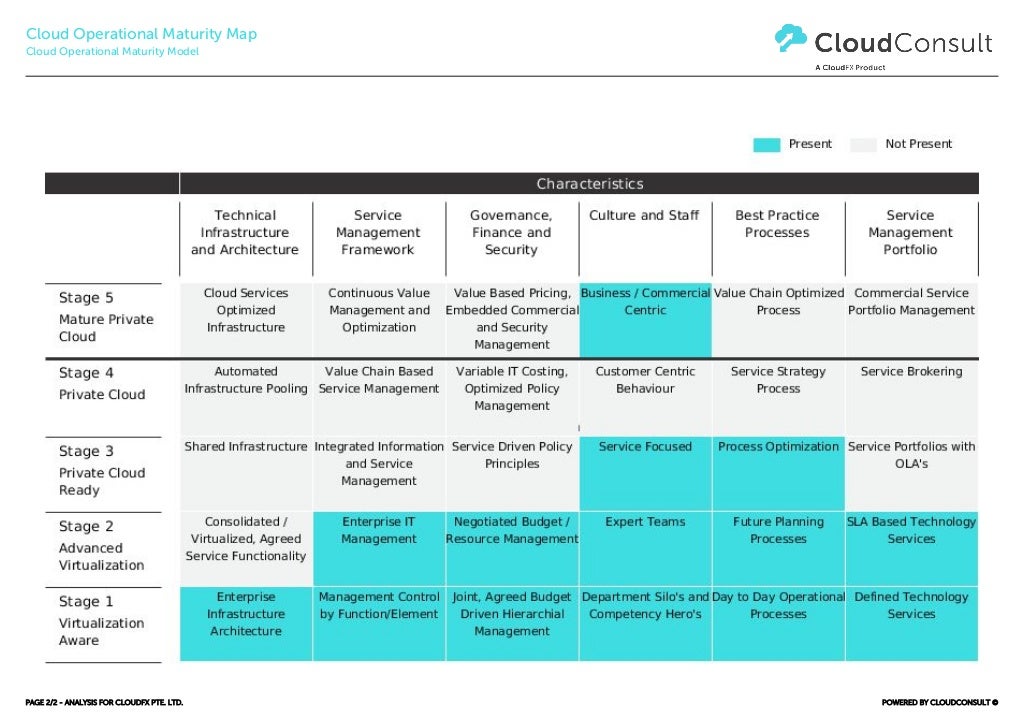

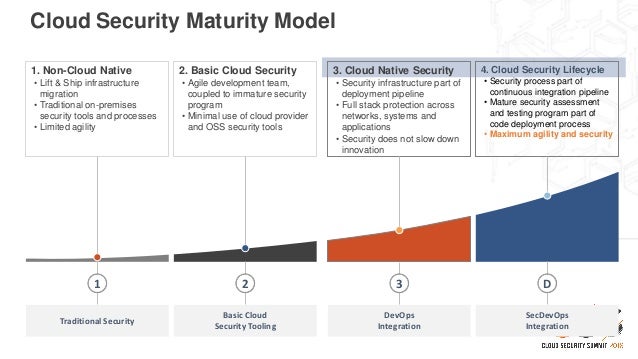
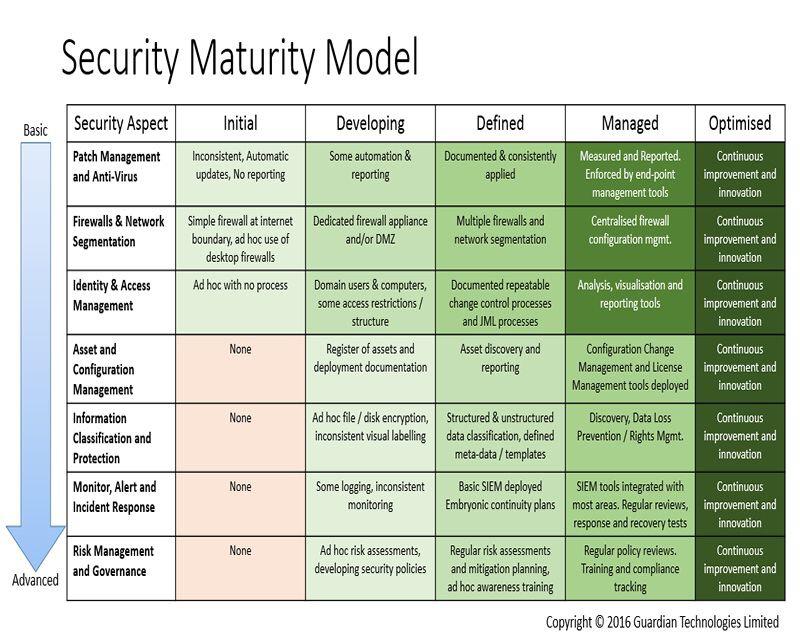
.png?width=2000&name=MaturityModel_horz_v2%20copy%20(1).png)

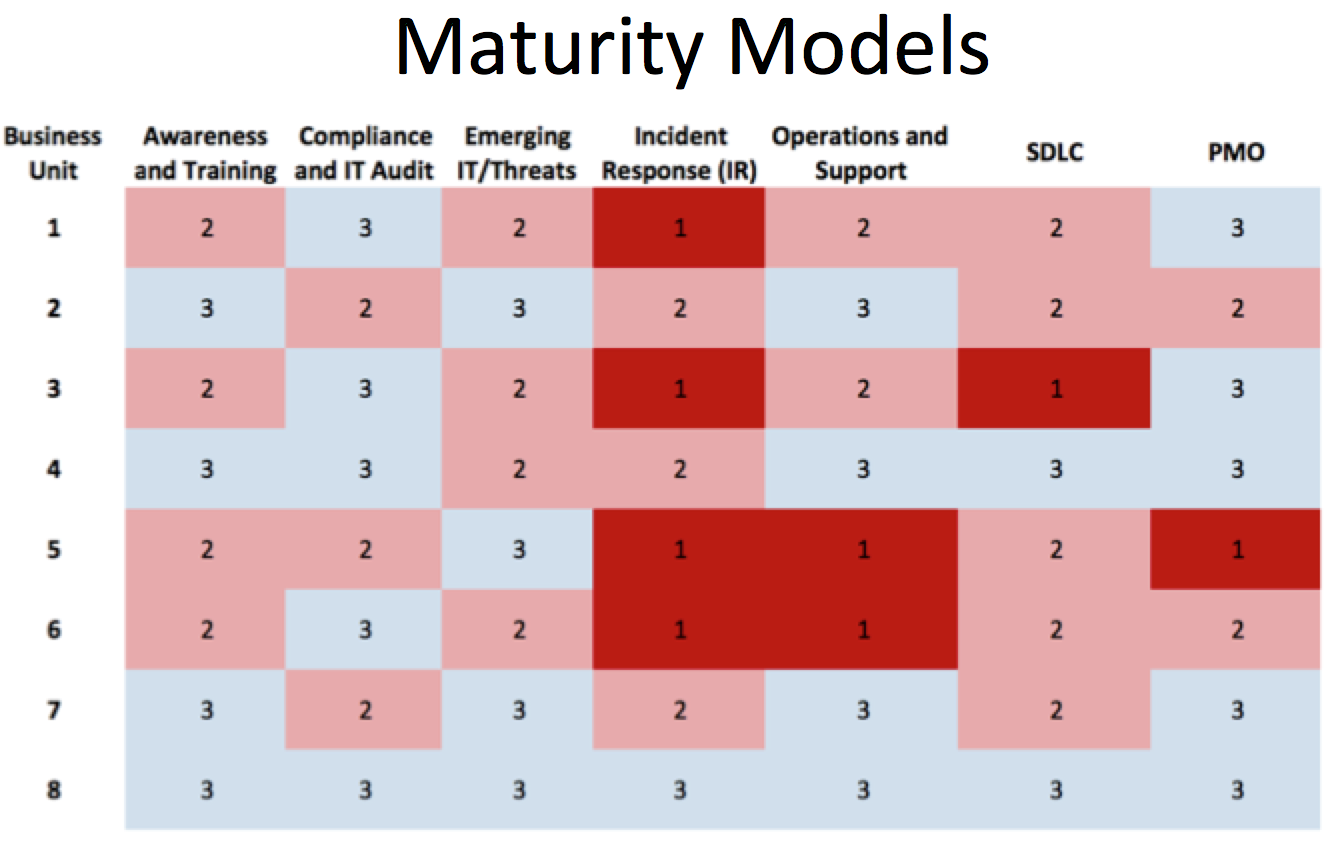
.png)


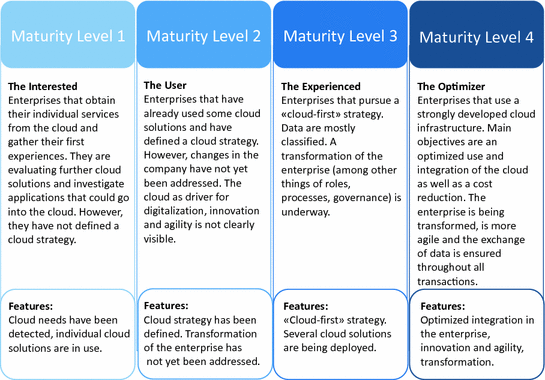









Post a Comment for "Cloud Security Maturity Model"